Celebrating 2nd Homelab Birthday
It’s the second homelab cakeday!
I’ve had a lot of fun with this little machine of my own over the past two years, and I never got to truly appreciate it.
It started out as a dumb box for me to tinker with Linux after my military service because I was bored and had nothing to do. It was supposed to run a few websites and services and nothing more.
Over time, it grew to be much more than that: it’s now my personal streaming service, cloud storage, statistics machine and so on. It has been a crucial part of my life. So in the hopes that this post will help you to finally get your own homelab and be a happy man as I am, here’s a brief overview of what/how my homelab is run.
Docker
I run everything, including Caddy, as Docker containers because they’re so easy to set up and reproduce. I have set up docker-compose.yaml files for basically every service I run and when there’s a need for an update or changes, I can just fix the compose file and docker compose up -d my way. It’s such a game-changer in terms of self-hosting.
Networking
Access
One of the many benefits of homelabbing is that you can ultimately trust the server to be private: but that is only when you secure it properly, and it’s damn hard to do so.
The best way to do this is to never expose anything to the Internet. That, however, comes with major disadvantage of either getting bound by the proximity to the server and its LAN or having to open a VPN server which is ultimately, opening something to the Internet.
Luckily, services like Zerotier or Tailscale exist and they are exactly what you will need. I’m using Tailscale after using Zerotier for about a year because of its more polished looking UI and app but Zerotier has its own benefits as well. Either way, they are well-documented, battle-tested and best of all, free.
Proxy & DNS
Having a proxy is, in my opinion, a necessity when it comes to homelabbing. It acts as another layer of security and we can’t have enough of them. You’ll also probably need it regardless of its security benefits because your services will grow.
I’ve been using Caddy with Cloudflare, and it works great. I had used NginxProxyManager for some time until I decided that I really don’t need web UI and that it was quite a hassle to set up internal SSL stuff (I’m sure that it’s doable and it’s not as hard as I thought, but why bother?).
archive.lan {
tls internal
reverse_proxy archivebox:{port}
}Mixed with Pihole as an internal DNS, I was able to use the .lan1 domain for my internal stuff as well. .lan is (obviously) only accessible when I’m connected to Tailscale, so services behind .lan are pretty secure, and so far, I had no problem with their security (knocks on wood).
Backup / etc
I’m using Restic + Backblaze to back things up periodically. There’s not much to say about this since it’s very simple and easy to set things up. Luckily, I haven’t had any incidents that needed the backup yet, but I’m pretty sure that it will happen, and it most definitely will save my ass when it happens.
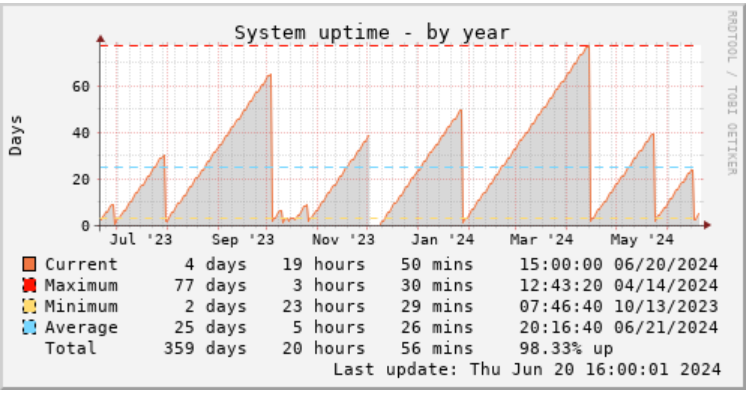
In the age of cloud computing, which is not only for tech bros in California anymore, having a safe place that is truly mine holds its value even more so. Cloud is just someone else’s computer, and there are limits to how much you can trust them. It’s nice to know that I have this small island of my own that I can do literally anything I want, on this vast sea that is the Internet.
Hoping to celebrate the next milestone at 3rd cakeday!
-
I’ve learned the hard way that I should stop using
.localfor intenral stuff. ↩︎